Compliance Services
Security Training Services in Washington, DC by ETTE
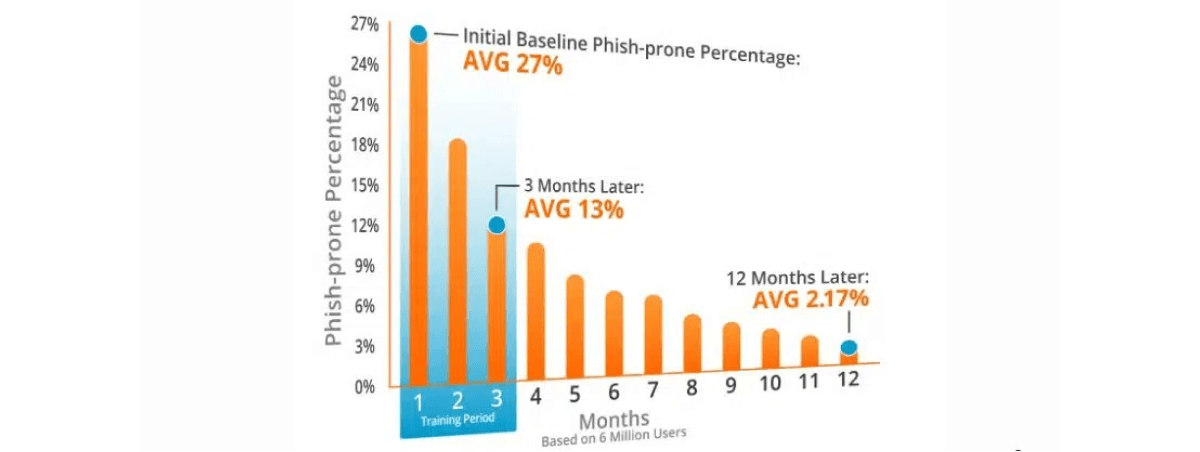
Benefits of Security Training at ETTE
The Human Factor in Preventing Data Breaches – Security Training
There are several programs an IT professional can implement to make their organization’s IT infrastructure less vulnerable to a cyber attack. However, recent evidence indicates an educated user base may be the best line of defense, making security training essential for companies. According to the 2018 Cost of Data Breach, a study conducted by Ponemon Institute, 25% of data breaches in the U.S. are triggered by human error. These errors include misdirected email, failure to delete sensitive data when finished using it properly. Intentional but non-malicious actions by staff, such as permitting unauthorized access, data disclosure to a trusted colleague or friend, or merely snooping is an avoidable source of breaches. An additional 30% of data breaches come as the result of “Social Engineering.” Social engineering breaches are efforts by hackers to manipulate unwitting users to provide credentials to allow illegal access to a secure system.
Social Engineering Techniques
There are several techniques hackers use to get a user to provide information, making security training essential. Some of the most common forms are: