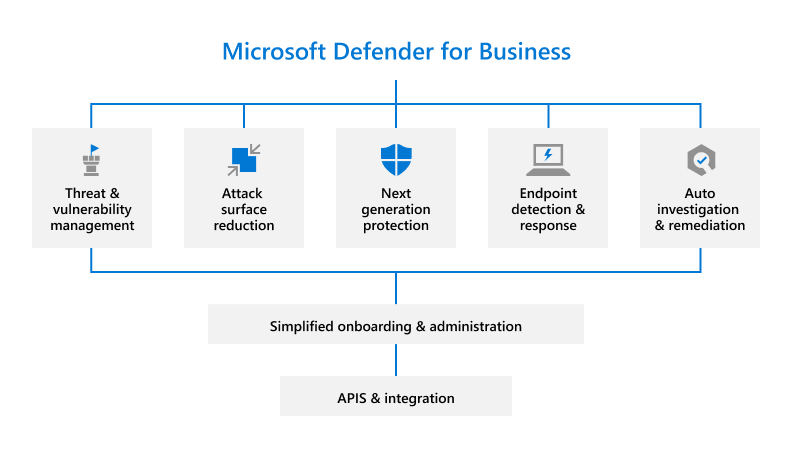
A good anti-virus program has always been an element of endpoint protection. Many antivirus programs use an approach called signature recognition. The antivirus software recognizes the signature IT profile of a particular form of attack and then shuts it down. The problem with this approach is that hackers constantly invent new attack methods that use unrecognized signatures, often called “zero-day” malware. Until the signature is identified, signature recognition antivirus does not stop the new attack. An NGEP system uses artificial intelligence (AI) to learn what a “normal” state is for your organization’s unique IT environment (traffic, connected devices and data flow). NGEP antivirus searches for deviations, which may constitute potential threats. The system then performs tests to decide whether the deviation is an acceptable anomaly, or should be elevated to the status of a potential threat. For threats, Next-Gen Endpoint Protection antivirus sends a warning message to the professionals who monitor the system. Some NGEP systems may use both AI and signature recognition as a “belt and suspenders” security approach. But, an effectively programmed AI engine would not require signature recognition, and large databases of attack signatures may consume unnecessary IT resources.
The proliferation of smart devices creates new and unique challenges for endpoint protection. Today, non-traditional devices such as television sets, credit card readers and home security systems have the potential to become vulnerable network endpoints. The simple USB port is the most commonly overlooked potential endpoint vulnerability. Users may unknowingly or deliberately connect any number of malicious devices to a USB port. An NGEP system recognizes and carefully monitors any new and unfamiliar equipment users add to the IT environment, including USB plug-ins. Even with trusted connected devices, the Next-Gen Endpoint Protection uses more of a “trust but verify” approach over a blind trust approach. This approach can be effective in stopping insider attacks using trusted devices.
One of the things that sparked the idea of NGEP was the criticism that a lot of security applications were effective in containing attacks and contaminations, but did little to help prevent attacks from occurring in the first place. NGEP systems typically include a number of features that enable them to prevent attacks. One typical feature is the creation of a “sandbox”, which is a virtual environment walled off from the rest of the network. When an unfamiliar app or data packet enters the system, Next-Gen Endpoint Protection systems first test it in the sandbox to ensure the packet is not malware or malicious code. If the packet is malicious, the system deletes the sandbox and rejects the packet. Other systems use proprietary AI algorithms to seek out anomalies and test questionable devices before hackers can launch an attack. All this said, a good NGEP system still needs good reactive defenses to prevent the spread of viruses that may evade the system, and help restore systems to pre-attack states.
Next-Gen Endpoint Protection often requires the ability for a system to create a large data set to perform a proper analysis of the IT environment and track all the endpoints. That data must be accessible, active and available for analysis. Systems that require an on-site physical device to present this data can cost an organization thousands of dollars in unnecessary data storage. IT Systems that depend on physical data storage for access and retrieval may not be fast enough to stop an attack as it unfolds.