Navigating the Compliance Landscape
NIST CMMC compliance refers to meeting the cybersecurity requirements outlined in both the National Institute of Standards and Technology Special Publication 800-171 (NIST SP 800-171) and the Cybersecurity Maturity Model Certification (CMMC) frameworks. Here’s what you need to know:
| Framework | Purpose | Requirements | Who Needs It |
|---|---|---|---|
| NIST SP 800-171 | Protects Controlled Unclassified Information (CUI) | 110 security controls across 14 families | Organizations handling CUI in non-federal systems |
| CMMC | Verifies implementation of cybersecurity practices | Three levels of increasing security | Defense contractors and subcontractors |
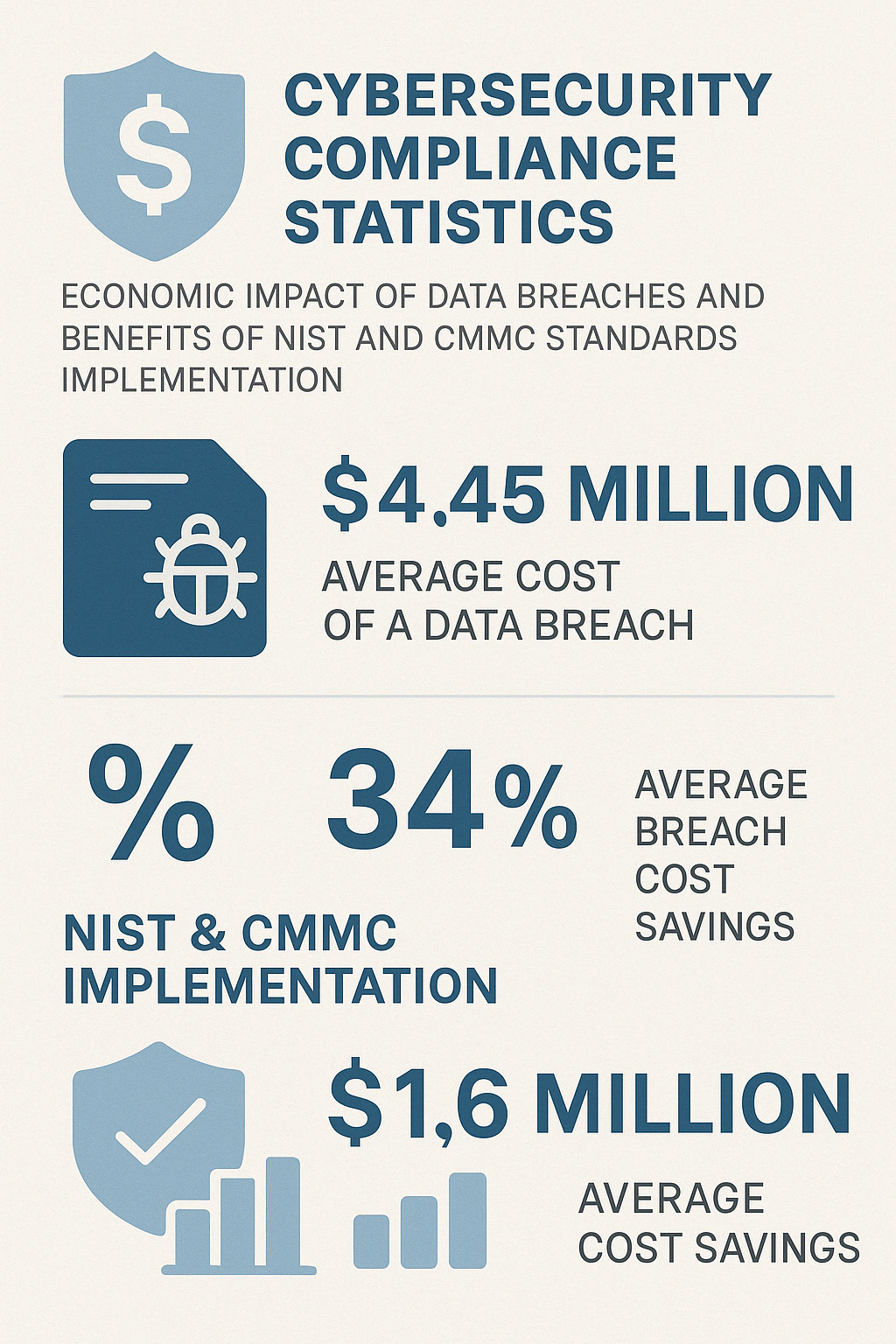
Let’s be real. In today’s hyperconnected world, cyber threats are lurking around every corner. For organizations working with the Department of Defense or handling sensitive government information, achieving NIST CMMC compliance isn’t just about checking boxes—it’s about protecting vital national security interests and ensuring your organization can continue winning federal contracts.
“DON’T GET CAUGHT WITHOUT CMMC COMPLIANCE. FAILURE TO DO SO COULD COST YOUR COMPANY ITS FEDERAL CONTRACTS,” warns a stark reminder from industry experts. This isn’t an exaggeration—over 300,000 companies in the Defense Industrial Base must now demonstrate compliance with increasingly stringent cybersecurity standards.
For small organizations with limited IT resources, these requirements can seem overwhelming. But breaking down the compliance journey into manageable steps can turn this challenge into an opportunity to strengthen your overall security posture.
In this guide, we’ll walk you through the essentials of NIST CMMC compliance, from understanding the basics to implementing practical solutions that won’t break your budget or overwhelm your team.
Nist cmmc compliance vocab to learn:
– cmmc control families
– dfars and nist 800 171
– nist sp 800 171 requirements
Understanding NIST SP 800-171 and CMMC: The Path to Compliance
Let’s face it—navigating NIST CMMC compliance can feel like trying to read a map in a foreign language. But don’t worry! We’re here to make this journey a lot more straightforward.
Both NIST SP 800-171 and CMMC were created with one critical mission in mind: protecting sensitive government information when it’s in the hands of non-federal organizations like yours. With cybercrime costing the global economy over $600 billion annually, and the Defense Industrial Base (DIB) losing between $57-109 billion each year to intellectual property theft, these frameworks aren’t just bureaucratic red tape—they’re essential shields for our national security.
The Role and Purpose of NIST SP 800-171
Think of NIST SP 800-171 as the foundation of your cybersecurity house. Developed by the National Institute of Standards and Technology, this framework focuses on protecting Controlled Unclassified Information (CUI) in non-federal systems.
“But what exactly is CUI?” you might ask. It’s information that requires safeguarding according to government policies but isn’t classified as top secret. In simpler terms, it’s sensitive but not classified—things like technical drawings, specifications, or personal data that could cause harm if they fell into the wrong hands.
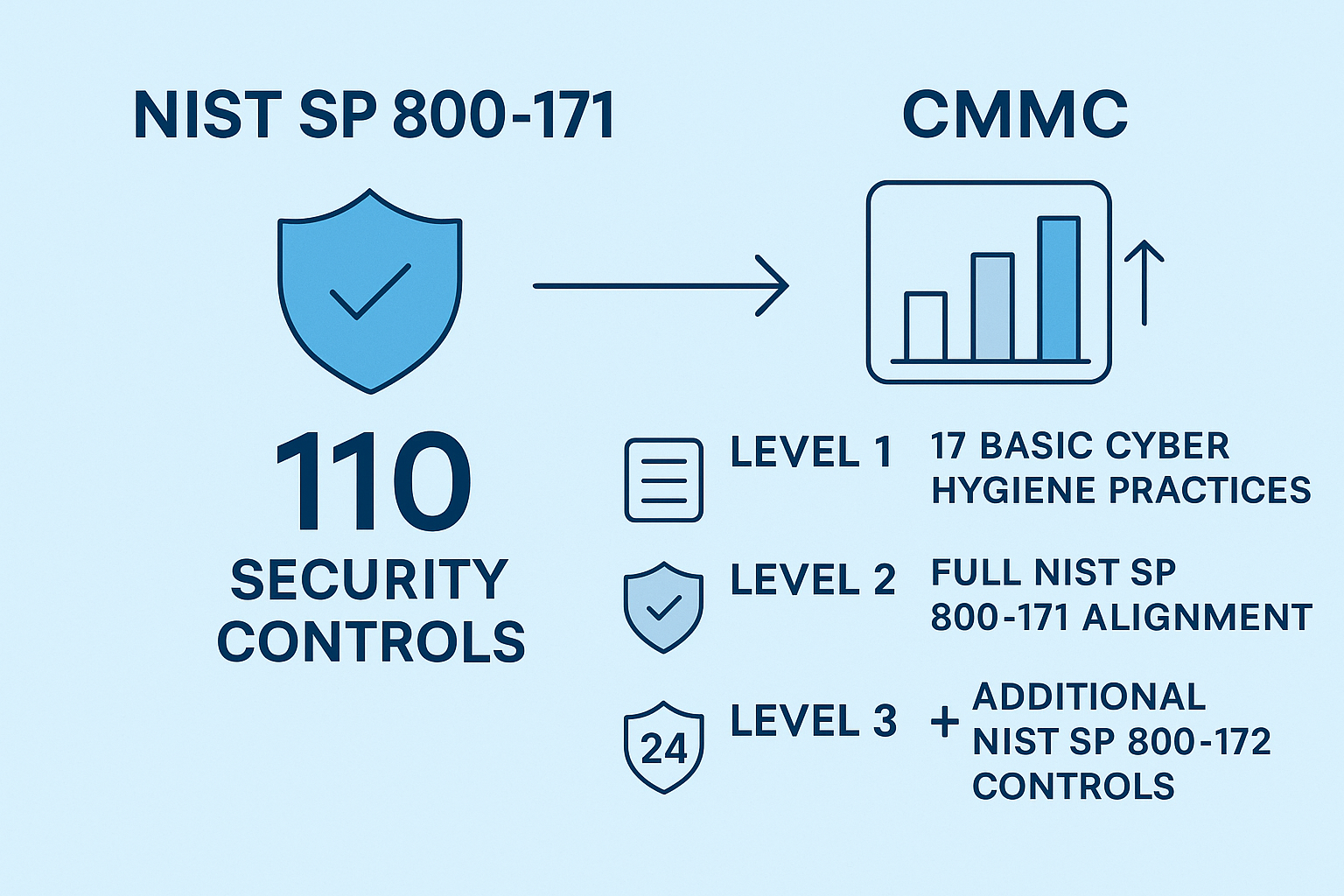
NIST SP 800-171 gives you 110 security requirements organized into 14 control families—from Access Control to System and Information Integrity. These requirements come in two flavors:
- Basic Security Requirements: The must-haves derived from FIPS 200
- Derived Security Requirements: The more detailed controls coming from NIST SP 800-53
Under DFARS Clause 252.204-7012, if you’re a defense contractor, implementing these controls isn’t optional—it’s mandatory. Previously, you could simply self-attest to compliance, but as one industry expert perfectly put it: “NIST SP 800-171 only states what must be done, whereas CMMC confirms that it has been done through independent certification.”
For the complete details, check out the NIST SP 800-171 official document.
Introducing CMMC: Enhancing Cybersecurity Maturity
If NIST SP 800-171 is the foundation, then CMMC is the whole house—complete with security systems and regular inspections. The Department of Defense developed CMMC because they realized self-attestation wasn’t enough to ensure companies were actually implementing proper cybersecurity controls.
CMMC takes things up a notch by introducing formal third-party assessments, establishing a clear maturity model, and strengthening supply chain security requirements. The current version (CMMC 2.0) features three progressive levels:
Level 1: Foundational Cyber Hygiene focuses on protecting Federal Contract Information with 17 basic practices. It requires annual self-assessment and aligns with FAR Clause 52.204-21—think of it as “Cybersecurity 101.”
Level 2: Advanced Cyber Hygiene incorporates all 110 security requirements from NIST SP 800-171. Depending on the sensitivity of the information you handle, you might need either a self-assessment or a third-party assessment by a CMMC Third Party Assessment Organization (C3PAO) every three years.
Level 3: Expert Cyber Hygiene builds on Level 2 by adding about 24 additional security requirements from NIST SP 800-172. This level is designed to protect against Advanced Persistent Threats (APTs)—the sophisticated hackers who don’t give up easily. It requires certification by the Defense Industrial Base Cybersecurity Assessment Center (DIBCAC).
What makes CMMC stand out is its shift from “trust me, I’m compliant” to “show me you’re compliant.” This verified approach helps ensure everyone in the defense supply chain is actually implementing the security controls they claim to have.
For more details, visit the Official DoD CMMC Page.
Key Differences Between NIST SP 800-171 and CMMC
While CMMC builds on the foundation of NIST SP 800-171, they’re not identical twins—more like parent and child. Here’s how they differ:
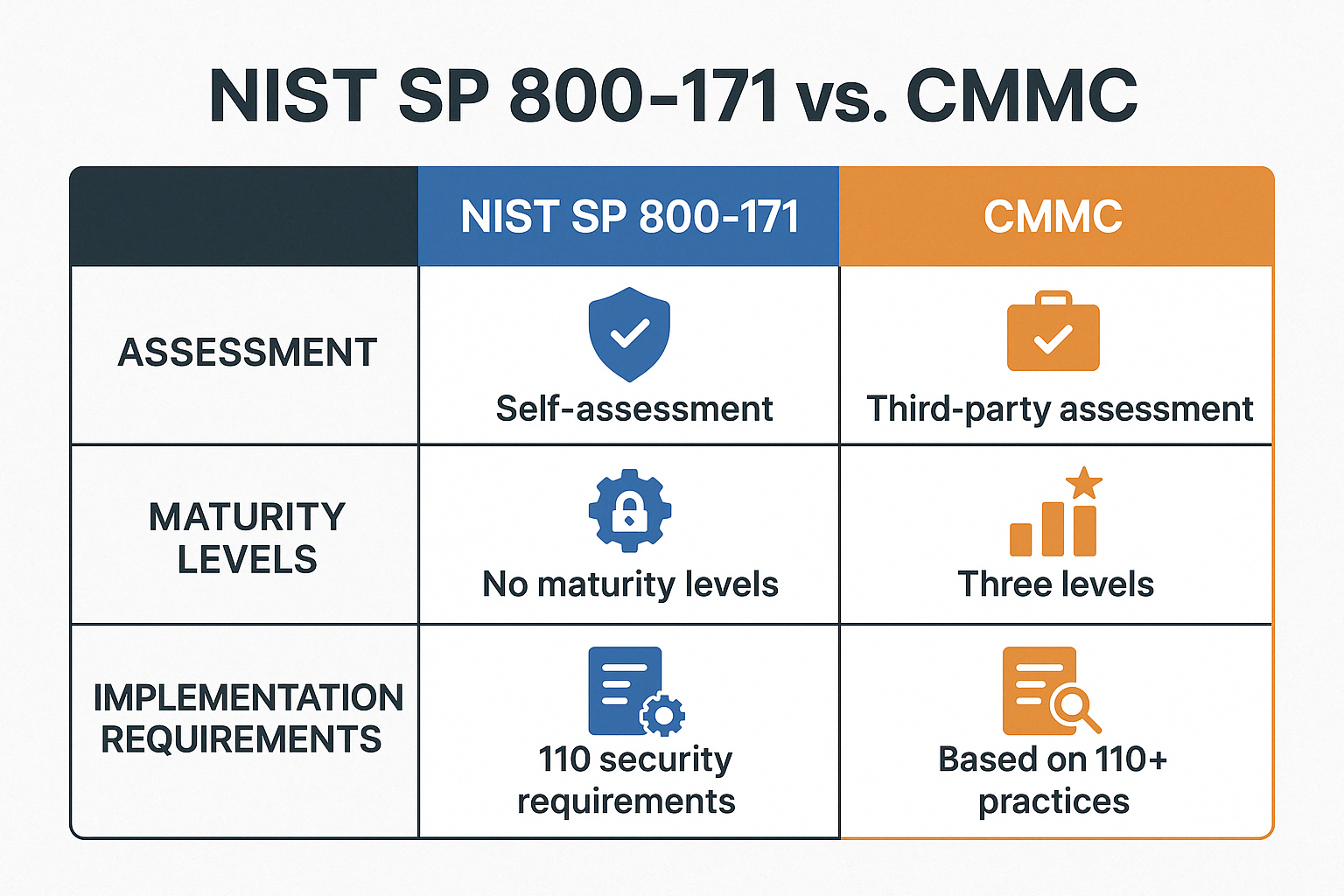
The most significant difference lies in how compliance is verified. With NIST SP 800-171, you’re essentially grading your own homework through self-assessment. CMMC, however, brings in an independent teacher to evaluate your work, especially at higher levels.
Another key distinction is CMMC’s structured maturity model. Rather than an all-or-nothing approach, CMMC offers a clear pathway for growth—from basic cyber hygiene practices to advanced protection against sophisticated threats. This allows your organization to improve steadily over time rather than trying to implement everything at once.
NIST CMMC compliance isn’t an either/or situation. CMMC doesn’t replace NIST SP 800-171; it builds upon it and verifies that you’ve properly implemented the controls. Think of NIST as the recipe and CMMC as both the cooking process and the taste test.
For defense contractors, especially smaller businesses with limited resources, understanding these frameworks is the first step toward developing a practical, effective compliance strategy. And remember—while compliance may seem daunting at first, it ultimately strengthens your security posture and makes you a more valuable, trusted partner in the defense supply chain.
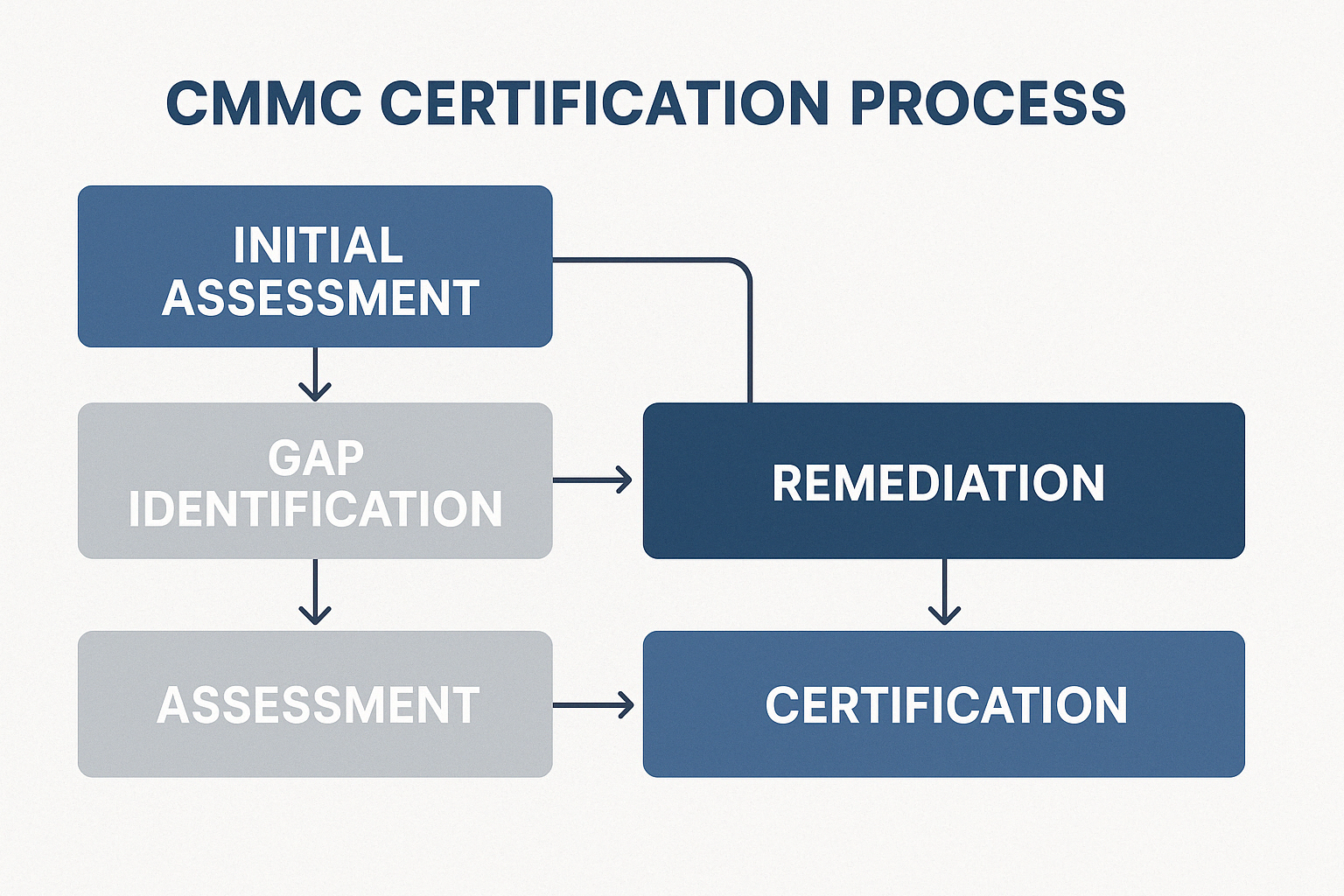
Steps to Achieve NIST and CMMC Compliance
The journey toward NIST CMMC compliance doesn’t have to feel like climbing Mount Everest. With a structured approach, you can break this complex process into manageable steps that address both technical requirements and organizational procedures. Let’s walk through how to make this journey less daunting.
Assessing Your Current Cybersecurity Posture
Before you can improve your security stance, you need to know where you stand. Think of this as taking inventory before a big home renovation project—you need to know what you’re working with.
Start by identifying exactly where Controlled Unclassified Information (CUI) lives in your organization. This means pinpointing what types of CUI you handle, where it’s stored, who can access it, and how it moves through your systems.
Many organizations make the mistake of trying to secure everything at once. As one expert wisely notes, “Focusing on limiting the CUI data footprint is a more manageable and effective method compared to attempting enterprise-wide compliance.” By carefully defining your CUI boundaries, you can significantly reduce the scope—and cost—of your compliance efforts.
With your CUI identified, it’s time for a thorough gap analysis using NIST SP 800-171A assessment procedures. This isn’t just a checkbox exercise—it involves interviewing your team members, testing your current controls, and documenting where you stand against the 110 requirements.
NIST scoring starts with a perfect 110 points and subtracts for each unimplemented control. Not all controls are created equal—some are worth 5 points, others 3 or just 1. And partial implementation gets you zero credit. As the assessment guidance bluntly states, “A plan of action is not a replacement for a completed requirement.”
After your gap analysis, prioritize your remediation efforts strategically. Focus first on high-value controls (those worth 5 points), then on controls addressing critical security risks, and finally on those that serve as foundations for other requirements.
Implementing Required Controls and Practices
Now comes the hands-on part of your NIST CMMC compliance journey—implementing the controls and practices needed to close those gaps.
First, develop comprehensive documentation. In the compliance world, there’s a saying that rings absolutely true: “If it is not documented then it does not exist.” Start with a detailed System Security Plan (SSP) that describes your system boundaries and explains how you address each requirement. Create clear policies that express management’s security intentions, procedures that provide step-by-step instructions, and guidelines that offer recommended approaches.
On the technical side, focus on implementing robust controls in several key areas. Establish strict access controls based on the principle of least privilege—users should only access what they need for their jobs, nothing more. Implement multi-factor authentication (MFA), especially for remote access and privileged accounts. MFA is a valuable 5-point control, and even partial implementation costs you 3 points.
Set up comprehensive logging and monitoring to track user activities and system events. Develop and maintain secure configurations for all your systems, including baseline configurations and change control processes. And don’t forget encryption—implement FIPS-validated cryptography for data both in transit and at rest.
The human element is just as important as the technical. Develop security awareness training for all personnel, establish robust incident response capabilities, and implement appropriate personnel screening procedures. And while it’s easy to focus on digital controls, don’t overlook physical security—limit physical access to systems processing CUI and properly protect media containing sensitive information.
With increasing focus on supply chain security, develop a Supply Chain Risk Management Plan to assess and manage risks associated with suppliers and service providers. Make sure your subcontractors handling CUI also comply with the appropriate requirements.
Preparing for Assessments and Certification
With controls implemented, it’s time to prepare for the formal assessment process. This is where your hard work gets validated.
Begin with a thorough self-assessment using the objectives and methods in NIST SP 800-171A. Document evidence of compliance for each requirement—screenshots, policy documents, logs, anything that demonstrates you’ve implemented the control effectively. Calculate your score using the DoD Assessment Methodology and identify any remaining gaps.
For requirements you haven’t fully implemented, develop detailed Plans of Action and Milestones (POA&Ms). Each POA&M should clearly identify the deficiency, outline specific tasks to address it, allocate resources, set milestone dates, and include status tracking. Under CMMC 2.0, you may receive a “Conditional CMMC Status” with POA&Ms, but you’ll need to close these out within 180 days to maintain certification.
If you’re subject to NIST SP 800-171, you must submit your self-assessment results to the DoD’s Supplier Performance Risk System (SPRS). Your submission needs to include the assessment date, your summary score, the scope of the assessment, and plans for addressing any unimplemented controls.
For organizations requiring CMMC Level 2 or Level 3 certification with third-party assessment, additional preparation is necessary. Engage early with a C3PAO or DIBCAC to understand their approach. Conduct a pre-assessment review, ensure all documentation is up-to-date, prepare your team for interviews, and have evidence readily available for each control.
Overcoming Common Challenges in Compliance
Even the most well-planned NIST CMMC compliance journey will face obstacles. Let’s look at common challenges and practical ways to overcome them.
Resource constraints hit small and medium-sized businesses particularly hard. When budget, staff, and expertise are limited, start with the highest-priority controls that address critical security risks. Consider implementing in phases rather than all at once. Don’t hesitate to leverage external expertise for specialized areas—this is where partners like ETTE can provide valuable support. Also explore cost-effective cloud solutions that already meet many compliance requirements.
The sheer complexity of 110 controls can feel overwhelming, especially if you’re new to formal cybersecurity frameworks. Break down controls into manageable components and use the assessment objectives in NIST SP 800-171A as implementation guidance. Focus on understanding the intent behind each control rather than just checking boxes. As one cybersecurity expert warns: “If you have never thought about security before and face NIST SP 800-171 compliance requirements, buckle up.”
Managing the scope of your CUI protection can dramatically impact both complexity and cost. Consider implementing network segmentation to isolate systems handling CUI, apply strict access management, and perhaps create a dedicated enclave for CUI processing. Document your system boundaries clearly in your SSP. As one implementation expert advises, “Limiting the scope of CUI to a singular, well-segmented system can significantly reduce the complexity and cost of compliance.”
Documentation requirements can feel like a paper mountain. Use templates and frameworks to streamline the process, implement a document management system for organization and version control, and assign clear ownership for each document. Critical compliance mantra: “If it is not documented then it does not exist.”
Finally, ensuring your supply chain meets compliance standards presents unique challenges. Include compliance requirements in contracts, develop a supplier assessment program, provide resources and guidance to key suppliers, and regularly review their compliance. Your security is only as strong as your weakest link—which might be a third-party provider.
The path to NIST CMMC compliance may seem steep, but with methodical planning and execution, it’s entirely achievable. More importantly, these steps don’t just help you meet regulatory requirements—they substantially strengthen your overall security posture, protecting your organization and your customers from increasingly sophisticated cyber threats.
Conclusion

The journey to NIST CMMC compliance isn’t a sprint—it’s a marathon that requires commitment, patience, and continuous improvement. As you’ve seen throughout this guide, achieving compliance involves understanding complex frameworks, implementing robust controls, and maintaining vigilant oversight of your security practices.
But here’s the good news: this journey is absolutely worth it.
Beyond just checking regulatory boxes, compliance strengthens your organization’s security foundation and builds trust with government partners. Each step you take—from identifying where CUI exists in your systems to implementing those 110 security controls—moves you closer to not just compliance, but genuine cyber resilience.
“Security is a journey, not a destination,” as cybersecurity experts often remind us. And they’re right. The cyber threat landscape continues to evolve at breakneck speed, with attackers constantly developing new techniques to compromise sensitive information. That’s why NIST CMMC compliance frameworks are designed as living documents that evolve alongside these threats.
Looking ahead, we’re seeing exciting developments in the compliance landscape. Automation tools are making continuous monitoring more manageable, while improved supply chain security practices are helping organizations extend their security umbrella to partners and vendors. The shift toward maturity-based frameworks reflects a growing understanding that security isn’t just about what you implement—it’s about how effectively those controls operate in your unique environment.
At ETTE, we’ve walked this path with many small businesses and non-profits who initially felt overwhelmed by compliance requirements. As a minority-owned business based in Washington, DC, we understand the unique challenges that organizations with limited resources face. We’ve seen how breaking these complex standards into manageable steps can transform the seemingly impossible into the entirely achievable.
Our approach is simple: we meet you where you are. Whether you’re starting from scratch or looking to improve existing security practices, our team brings the expertise and support you need to steer the complexities of NIST CMMC compliance without disrupting your core mission.
Effective cybersecurity should empower your organization—not burden it. With thoughtful implementation and the right support, compliance becomes an asset rather than an obstacle.
For more detailed information about how we can support your compliance journey, visit our NIST 800 Compliance Services page. Our team is ready to help you transform compliance challenges into opportunities for growth and improvement.
As one of our clients recently told us, “Compliance seemed impossible until we broke it down into manageable steps.” With patience, persistence, and the right partner by your side, your organization too can build a security program that not only satisfies regulators but truly protects what matters most.