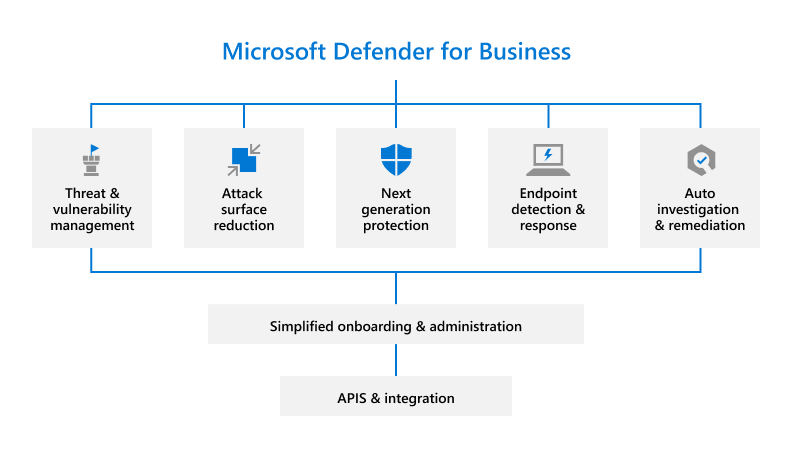
A good anti-virus program has always been an element of endpoint protection. Many antivirus programs use an approach called signature recognition. The antivirus software recognizes the signature IT profile of a particular form of attack and then shuts it down. The problem with this approach is that hackers constantly invent new attack methods that use unrecognized signatures, often called “zero-day” malware. Until the signature is identified, signature recognition antivirus does not stop the new attack. An NGEP system uses artificial intelligence (
AI) to learn what a “normal” state is for your organization’s unique IT environment (traffic, connected devices and data flow). NGEP antivirus searches for deviations, which may constitute potential threats. The system then performs tests to decide whether the deviation is an acceptable anomaly, or should be elevated to the status of a potential threat. For threats, Next-Gen Endpoint Protection antivirus sends a warning message to the professionals who monitor the system. Some NGEP systems may use both AI and signature recognition as a “belt and suspenders”
security approach. But, an effectively programmed AI engine would not require signature recognition, and large databases of attack signatures may consume unnecessary IT resources.